In this article, you’ll learn all about TLS fingerprinting and how Bright Data, a company offering web data collection, unblocking solutions, and proxy services, utilizes it to mask proxies and enhance web scraping.
Understanding TLS Fingerprinting
TLS is a popular encryption protocol commonly used in computer networks to secure connections between web clients and servers. When you start exploring and communicating with secure websites on the internet, the process kicks off with a TLS handshake:

Your web browser or client starts with a connection request that needs to be acknowledged by the server. The TLS handshake then initiates with the client sending a ClientHello message to the website’s server. This message contains information about the web browser’s capabilities and preferences, such as supported cipher suites, extensions, and TLS versions. The website server receives this message and compares the list of cipher suites in the ClientHello message with the list of ciphers supported by the server. Then the server responds with its own Hello message, containing its TLS protocol, the chosen cipher suite, and the server’s security certificate, which includes the server’s public encryption key.
The client verifies the server’s security certificate with the certificate authority that issued it, then responds with a premaster secret key, which is encrypted using the web server’s public key. The server decrypts the premaster secret, and both the client and server can generate a session key, creating a secure connection for web browsing. For example, the following is the TLS certificate that is sent when you open https://brightdata.com/:

Each web browser or client uses a different TLS library with a unique combination of supported cipher suites and extensions. For instance, Firefox relies on the Network Security Services (NSS) library; Chrome uses BoringSSL, which is an open source TLS library created by Google; Python uses the OpenSSL library; Safari uses Secure Transport, which is Apple’s custom TLS implementation; and Microsoft Edge uses Schannel.
Using the information from a client’s Hello message, a TLS fingerprint can be calculated and compared against the expected TLS library configuration for the various web browsers:
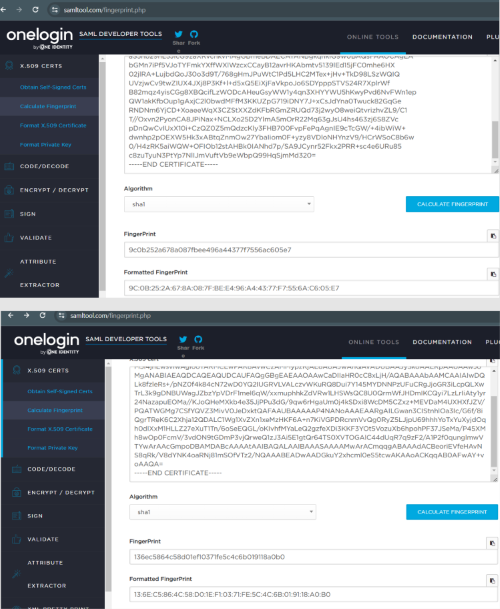
This fingerprint can be used to help identify clients, their web browsers, and operating systems. It can also monitor for abnormal requests when user headers don’t match their TLS fingerprint.
TLS Fingerprinting and Proxy Anonymity
TLS fingerprinting is another method in a string of continuous attempts by web companies and organizations to control and secure their web traffic effectively. It’s aimed at restricting bots, web clients, and entire regions from accessing data or content. Simply masking your IP address, changing proxies, striping, or modifying user agent headers is no longer enough since TLS fingerprinting can still be used to identify the underlying client characteristics based on other handshake parameters, even if user-agent information is obscured. Each connection attempt can be referenced against a host of TLS fingerprints and classified as abnormal traffic.
Although TLS fingerprinting is a viable security measure for your web traffic, its effectiveness is not absolute. As more organizations create and utilize anti-bot measures that use TLS fingerprinting technology, new methods to bypass TLS fingerprinting are created.
Proxy services often aim to blend user traffic with legitimate traffic to avoid detection or blocking. Taking into account TLS fingerprinting measures, some proxy services, like Bright Data, provide proxies that mimic the TLS fingerprints of commonly used clients or applications, making the proxy traffic appear similar to genuine connections, enhancing anonymity.
Bright Data uses TLS fingerprinting as a component of its web scraping APIs. With simulated TLS fingerprints of genuine clients’ web traffic, Bright Data’s products ensure your web activity is indistinguishable from regular users accessing web resources. It boasts a consistent success rate and is continually updated by the Bright Data team to ensure consistently high performance. Additionally, Bright Data’s residential proxies are based on genuine resident internet users, enabling you to bypass regional restrictions.
TLS Fingerprinting and Web Scraping
In addition to its dual role in controlling and securing web traffic for web companies and enhancing anonymity for proxy service users, TLS fingerprinting gives organizations a fresh lens to analyze and explore their web traffic.
With TLS fingerprinting, new patterns of web traffic can be identified and classified into genuine or artificial web traffic. Repeated requests from web scrapers or bots can be identified by their TLS fingerprint and restricted from accessing websites. Additionally, bot traffic that presents with an inconsistent pairing of a TLS fingerprint and device class (OS, browser name, or browser version) can be easily identified as suspicious. For instance, a web scraper could project browser headers belonging to a Firefox client; however, its requests may not show the corresponding TLS fingerprint that Firefox browsers typically have.
To enhance this security feature, anti-scraping services collect comprehensive TLS fingerprint compilations and utilize these lists to identify common browser-like TLS signatures and blacklist common web-scraping fingerprints. Additionally, with the implementation of TLS fingerprints in anti-scraping measures, data collection platforms like Bright Data also maintain a collection of TLS fingerprints, leveraging these fingerprints of real web users to mimic genuine web traffic more effectively.
Bright Data utilizes TLS fingerprinting by exploring target websites and analyzing the specific fingerprinting techniques they employ to restrict traffic. Bright Data also offers a Web Scraper API, Scraping Browser and the Web Unlocker. The Bright Data Web Unlocker is a composite solution that avoids detection and restrictions from target websites and guarantees a 99 percent success rate for even the most sophisticated target websites. It offers proxy management and JavaScript rendering to give you consistent access to your chosen websites. The Web Unlocker also handles CAPTCHA solving, IP rotations, request retries, and cookie and fingerprint management, letting you skip through website blocking techniques in real time.
TLS Fingerprinting and Data Transmission
Finally, TLS fingerprinting is a quick and effective method to identify user clients. It is non-invasive and does not impede communication compared to security checks and restrictions, such as CAPTCHA, login/authentication forms, and deep packet inspection (DPI) checks. When using TLS fingerprinting as a security check, your web connection handles and processes data transmission without requiring decryption.
Many websites utilize non-invasive checks, such as TLS fingerprinting, IP address, and user behavior analysis, before triggering their more restrictive security measures. Projecting a valid TLS fingerprint for web traffic security is a good way to avoid triggering invasive checks and data transmission restrictions.
Bright Data ensures smooth data transmission by generating customized TLS handshakes at the network level and dynamically generating user-agent headers and other web traffic parameters to mimic real browsers’ requests. The Bright Data Web Unlocker optimizes website access and data transmission by intelligently handling fingerprinting, headers, and emulation, ensuring efficient and unobtrusive data collection.
Conclusion
TLS fingerprinting is a versatile tool that can be used for both web scraping and anti-scraping organizations. It enables organizations to enhance their analysis of web traffic patterns and enables better identification of potentially malicious activity. Additionally, businesses focusing on data collection can leverage TLS fingerprints to seamlessly integrate into a target website’s traffic, improving proxy anonymity and web scraping efforts.
The Bright Data Web Unlocker, Scraping Browser and Web Scraper API are practical examples of TLS fingerprinting in action, showcasing its benefits for anonymity and web scraping. Bright Data utilizes automated fingerprinting-mimicking techniques to unlock georestricted content and provide you with anonymous access to online resources. The Bright Data residential proxy network mimics common TLS fingerprints from real users to improve your scraping efficiency and reliability. This allows users to browse quickly and securely while avoiding detection and anti-scraping measures.






